Source: tomshardware.com
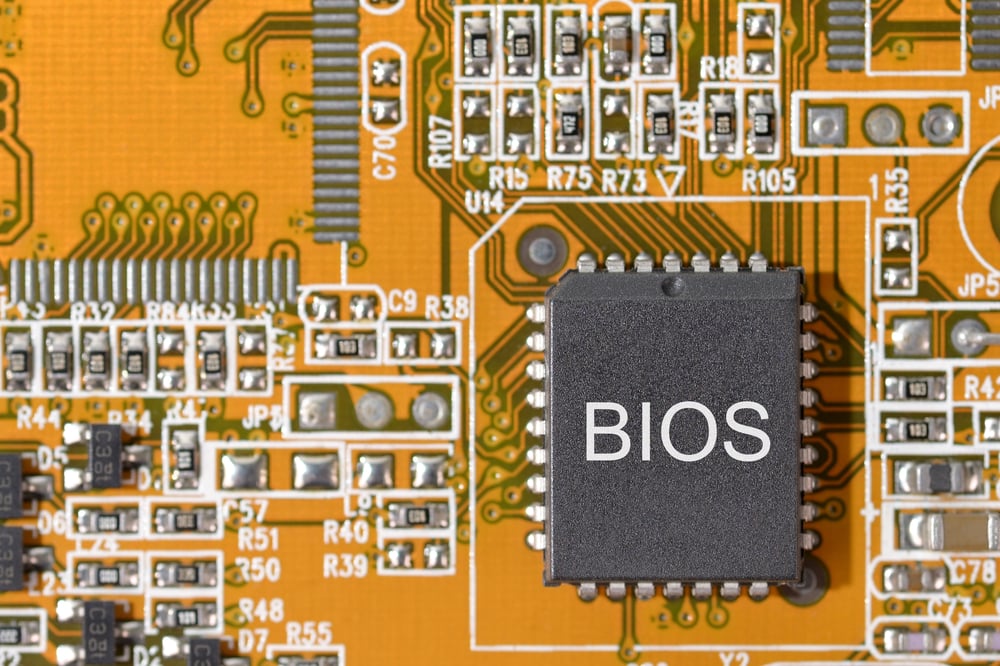
BIOS security is integral to the protection of critical information and ensuring unauthorized personnel cannot access or control your system.
In this blog, you’ll learn three ways to secure your BIOS to ensure your system is fully protected across the hardware, firmware, and software layer stack and achieves optimal performance.
What is a BIOS?
A BIOS, or Basic Input Output System, is a customized firmware component used during the booting process for hardware initialization and managing data flow between a computer’s operating system and attached devices.
Why should you secure your BIOS?
Cyberattacks have become increasingly sophisticated, and traditional safeguards are proving to be rather ineffective in the face of these advanced attacks.
If your BIOS is not secured, hackers can easily access and manipulate a computer’s information, gaining control over your system up to the highest level.
Oftentimes, these data breaches are very difficult to detect, even when using high-level scanning and other protective measures.
What are some methods to secure your BIOS?
There are three primary methods used to protect your BIOS : passwords, full disk encryption, and trusted platform modules.
- BIOS Passwords:
- The BIOS starts before the operating system (OS), so the user must enter a password before the OS and most other hardware is allowed to start. Then, they need to enter another password to access a computer’s features. Requiring two sets of passwords adds an extra layer of security against password-cracking tools that are used to bypass traditional security protections.
- Full disk encryption (FDE):
- This turns information in a storage medium into a secret format that can only be understood by people or systems authorized to access the information. All information on the system’s hard drive is transcribed from plaintext into ciphertext, protecting the entire disk volume and all files on the drive.
- Trusted Platform Module (TPM):
- This is a type of technology that provides hardware-based, security-related functions. A TPM chip is a secure crypto-processor that is designed to carry out cryptographic operations. The chip has multiple physical security mechanisms to make it resistant to tampering and malicious software.
- Some advantages of TPM technology are that you can:
- Generate, store, and limit the use of cryptographic keys.
- Use it for platform device authentication.
- Ensure platform integrity by taking and storing security requirements.
- The most common TPM functions are used for system integrity measurements and for key creation and use. During the boot process, the boot code is loaded along with firmware and OS components that can be measured and recorded in the TPM. These measurements can be used as evidence for how a system started and to make sure that a TPM-based key was used only when the correct software was used to boot the system.
- Full disk encryption makes use of the TPM chip on the motherboard to unlock the key.
The Trenton Advantage
A secure, custom BIOS aids in enhancing protection against unauthorized usage and other cyberattacks, as you can add the latest security technologies to lock down BIOS parameters and control.
At Trenton, we customize our parts and components from enclosure down to the BIOS, providing our customers with the latest in ruggedized, high-performance compute solutions to operate at maximum efficiency.
We also partner with companies like Intel and Star Lab to continually monitor security modifications and enhancements, so we can implement related fixes and updates quickly and efficiency to help you achieve optimal performance at any time, every time.
Want to learn more? Get in touch with our team of experts to craft a ruggedized, USA-made, cybersecure solution per your requirements to help you ensure mission success across the strategic, tactical, and operational levels.






 Users Today : 2
Users Today : 2 Users Yesterday : 4
Users Yesterday : 4 Users Last 7 days : 33
Users Last 7 days : 33 Users Last 30 days : 158
Users Last 30 days : 158 Users This Month : 104
Users This Month : 104 Users This Year : 1840
Users This Year : 1840 Total Users : 4452
Total Users : 4452 Views Today : 9
Views Today : 9 Views Yesterday : 14
Views Yesterday : 14 Views Last 7 days : 127
Views Last 7 days : 127 Views Last 30 days : 461
Views Last 30 days : 461 Views This Month : 338
Views This Month : 338 Views This Year : 4453
Views This Year : 4453 Total views : 11840
Total views : 11840 Who's Online : 0
Who's Online : 0